Configuring SAML SSO for UserEcho
These steps will guide you through setting up the single sign-on functionality between ADSelfService Plus and UserEcho.
Prerequisite
-
Log in to ADSelfService Plus as an administrator.
- Navigate to Configuration → Self-Service → Password Sync/Single Sign On → Add Application, and select UserEcho from the applications displayed.
Note: You can also find UserEcho application that you need from the search bar located in the left pane or the alphabet wise navigation option in the right pane.
-
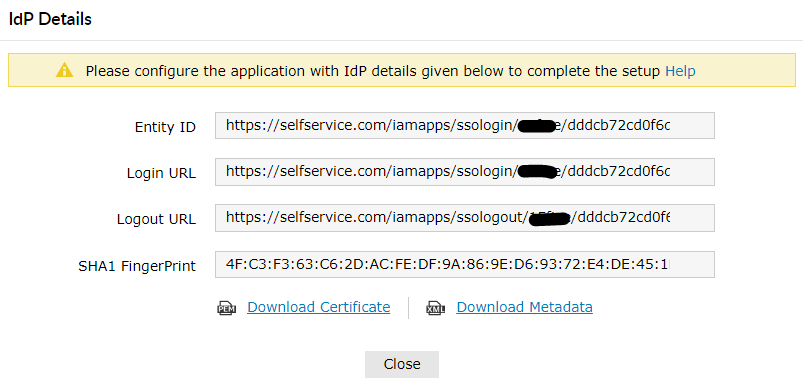
Click Download SSO Certificate link in the top-right corner of the screen.
-
In the pop-up that appears, copy the Login URL, Logout URL and download the SSO certificate by clicking on the Download Certificate button.
UserEcho (Service Provider) configuration steps
-
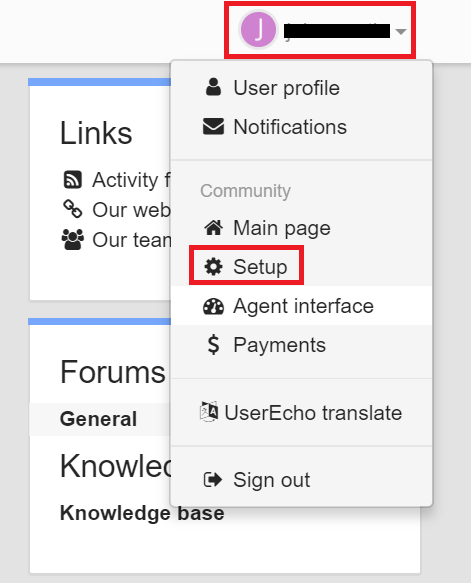
Login to UserEcho portal with an administrator’s credentials.
-
Click on Profile at the top-right corner and select Setup
-
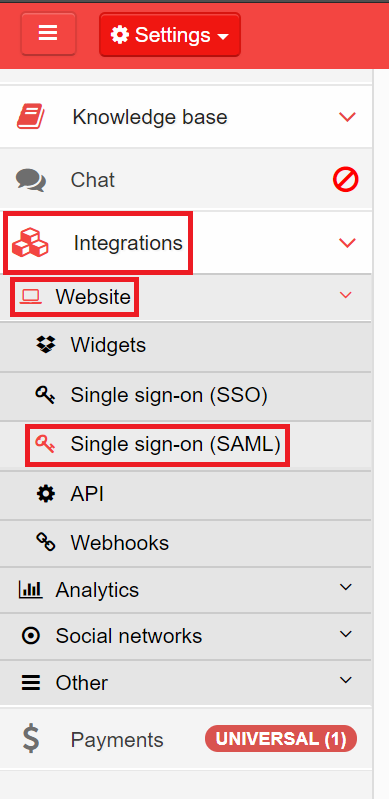
Select Integrations from the left pane and click on Single sign-on (SAML).
-
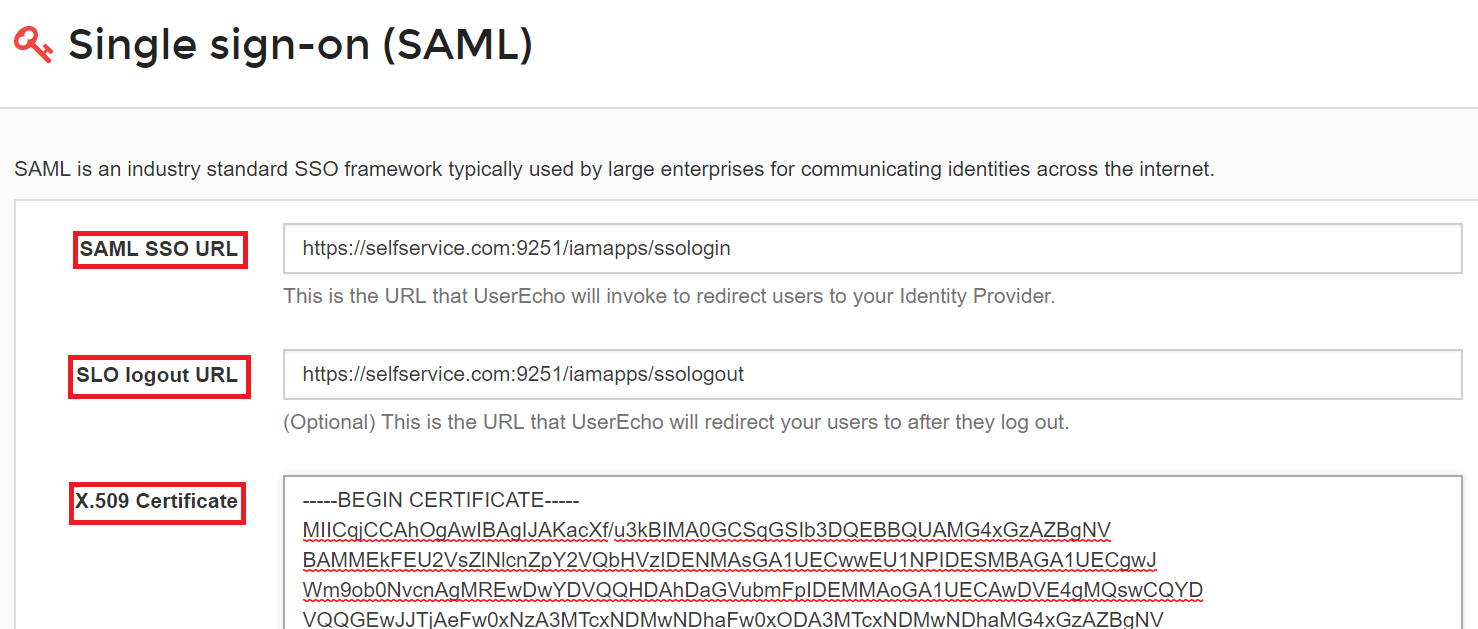
In the SAML SSO URL, enter the Login URL copied in Step 4 of Prerequisite,.
-
Open the SSO certificate downloaded (rsacert.pem ) in Step 4 of Prerequisite and paste its content in the X.509 Certificate field.
-
Click Save.
-
Navigate to Project → Login Settings from the left pane.
-
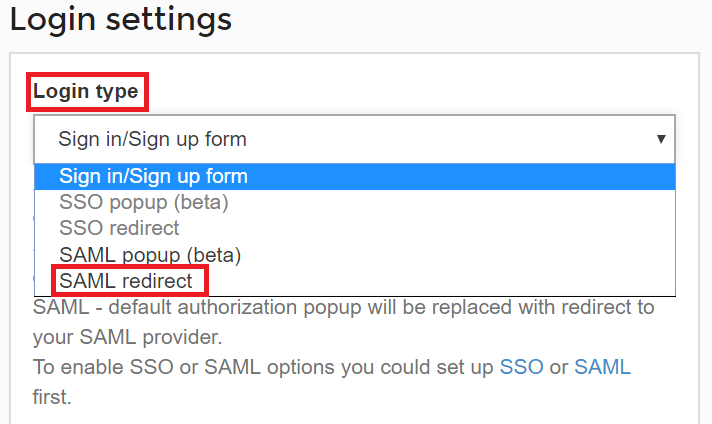
In the Login Type field, select SAML redirect from the drop-down box.
-
Click Save to complete the configuration.
ADSelfService Plus (Identity Provider) configuration steps
-
Now, switch to ADSelfService Plus’ UserEcho configuration page.
-
Enter the Application Name and Description.
-
In the Assign Policies field, select the policies for which SSO need to be enabled.
Note:ADSelfService Plus allows you to create OU and group-based policies for your AD domains. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy.
-
Select Enable Single Sign-On.
-
Enter the Domain Name of your UserEcho account. For example, if you use johndoe@thinktodaytech.com to log in to UserEcho, then thinktodaytech.com is the domain name.
-
In the SP Identifier field, enter the domain name of your UserEcho account. Example: If your UserEcho domain URL is https://test.userecho.com, your SP Identifier is test.
-
Choose the Name ID format that has to be sent in the SAML response. The Name ID format will specify the type of value sent in the SAML response for user identity verification.
-
Click Add Application
Your users should now be able to sign in to UserEcho through ADSelfService Plus.
Note:
For UserEcho, both IDP and SP initiated flows are supported.





